NAME Industria seguruaren laborategia 4.0
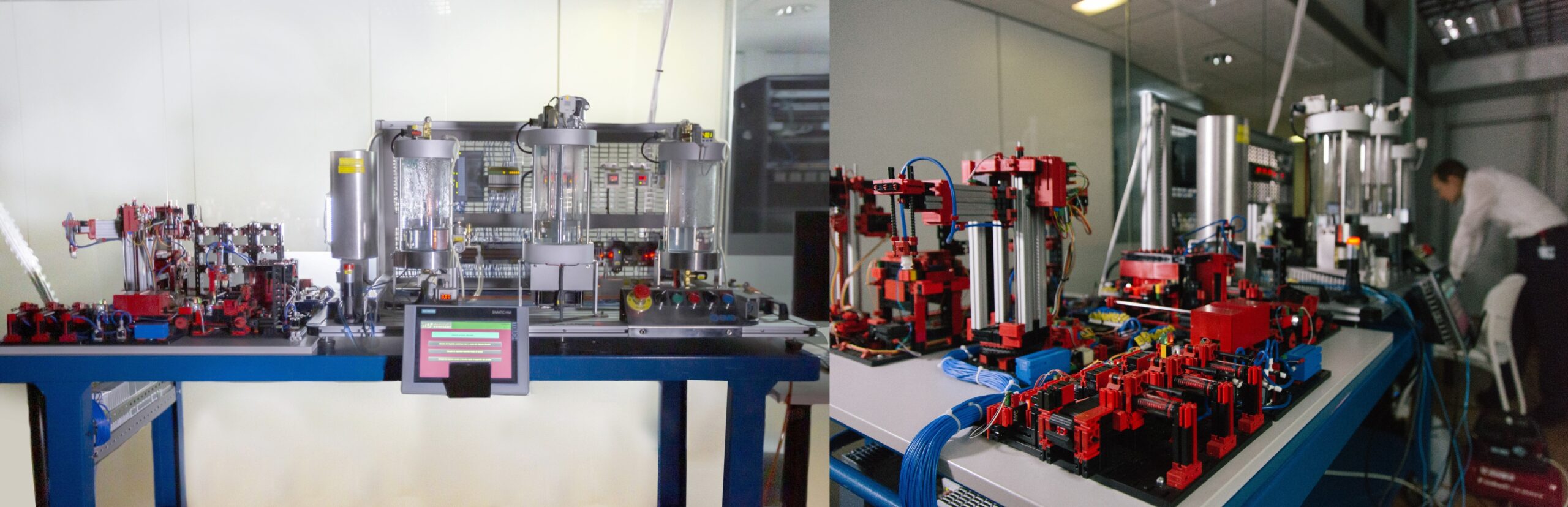
Aktibo hau fabrika adimenduna edo Smart Factory kontzeptura bideratutako proba bankuaren (edo testbed-aren) sorreran zentratzen da . Proba bankuaren helburuak honako hauek dira: - Helburu nagusia ziber-erasoak eta mehatxuak integratzea da, fabrikako produkzioaren antzeko ingurune bateko etapa eta prozesu ezberdinetan, baina eszenatoki erreal baten sortu daitezkeen ondorio kaltegarririk gabe. Kasu honetan, erlazionatutako helburuak hauek dira: - Sektorean kontzientzia maila handitzeko, produkzio prozesuetan ziber-erasoek izan dezaketen eragina erakutsi. - Eraso hauen aurrean, babeserako, detekziorako eta erantzuteko mekanismoak integratzea, garatzea eta balioztatzea. - Enpresetako segurtasun arduradunei ekipo errealekin formatzeko ingurunea ematea - Adimen artifizialeko eta analisi automatikoko teknikak aplikatzea mehatxuak detektatzeko. - Horrez gain, proposatutako proba bankuak beharrezko kontzeptu probak ahalbidetuko ditu, enpresek beren produkzio-ereduak Industria 4.0 eskemara modu seguruan eboluzionatzeko. Modu honetan, besteak beste, ondorengo aspektuekin lotutako erabilera-kasuak agerian utziz: - Bezeroak pertsonalizatutako ekoizpen pertsonalizatua - Ekoizpen-kate adimentsuak, komunikatuak, aldakorrak eta modu autonomoan konfigura daitezkeenak - Produktuen trazabilitate mekanismoak - Ekoizpen prozesuari lotutako datuen bilketa eta azterketa
FIELDS OF APPLICATION
Asset protection
Asset recovery
Identification of threats and risks
MOST OUTSTANDING EQUIPMENT AND COMPONENTS
-
Client application to customize product
A software application that allows the customization of the generated good. This information will be sent to the corporate network in order to be included in the production planning if applicable.
-
Cybersecurity subsystem
*Gatherer logs agents: These are lightweight software elements installed in various points of the IT and OT networks in order to collect information on the operational, communication or security applications launched in them. In principle, the use of Open Source Agents is considered since the commercial is not necessary.
*Intrusion detection and prevention systems (IDS / IPS): Software elements that allow the detection of unusual traffic patterns by setting standards, blocking them or generating alarms. Additionally, the use of Host IDS (HIDS) will be evaluated, which allows monitoring the status of a specific host and detecting threats within it.
*SIEM System is a software system for the collection, centralization and correlation of the information and events collected in the different logs by the agents. This allows the real-time analysis of information in order to launch alerts or detect threats. Both Open Source and commercial solutions will be contemplated.
*Industrial firewall is a Hardware Firewall focused on the specific needs of production environments, in which traditional networks (IT) coexist with those of production (OT). It is a specific Security Hardware. This element will also allow the monitoring of the OT network’s traffic internally and its interconnection with the OT network.
*Firewall IT: This firewall focuses on the general needs of an organization to protect from threats originated through Internet access. It is a commercial product to ensure an analogous environment to that of any company. It is a specific security hardware which will also allow to monitor the traffic entering and leaving the internet. -
Intelligent production line
It is intended to deploy a small production line that includes the necessary machines and devices to produce real products. This line would have several stations, including both the manufacturing and verification stages. The components of this line would communicate with the MES and the product to perform the action that corresponds according to the needs of the client. The components will communicate following the OPC-UA protocol, using the TSN protocol for their temporary synchronization. From an economic point of view, the line is the main component of the proposal. Its high cost is proportional to its importance. Having an environment similar to that of a real production is the only way to meet the above objectives. The production line includes hardware, software and communication elements. The following are also included:
• MES software which controls the production process at a high level, indicating what has to be produced. It is contemplated using it with an Open Source MES as well as the possibility of incorporating a commercial MES from the surrounding environment in order to validate potential cases that may occur in companies. It is a Software element that must be integrated in a PC within the perimeter of the OT network.
• ERP Software system that allows centralizing the corporate management, including the production planning, cost control, raw material inventories and traceability. -
Platform of Historization and Analytics
The generated data will be stored in the cloud complying with the necessary security measures (encryption, anonymization, transformation…). This data will be processed in the cloud, thus avoiding the installation and maintenance of IT infrastructure in the plant.
SERVICES OFFERED BY THE ASSET
IT/OT test environment to test new network or processing equipment in a controlled, realistic and high-stress environment
Before introducing new technology or devices into an end user’s productive network, such equipment can be introduced into the Industry 4.0 asset and tested for behaviour in an environment with varying degrees of hostility. In this way, its specific robustness can be evaluated, as well as the consequences it may have on the operation of the industrial processes affected. This asset focuses on providing an environment to test the behaviour of a system in relation to its own technological context, which would be the next step to the individual assessment of the system.
Realistic simulation of complete industrial environments, including IT and OT segments for testing cyber-defence against complex attacks
To configure the laboratory as a replica of the industrial information networks being used or those to be implemented in order to analyse the structural cybersecurity weaknesses and the specific impacts to which they are exposed in case of cyber-attacks. The features of the laboratory allow different degrees of simulation, depending on the effort required to replicate specific devices or processes on it. This will allow a better understanding of the vulnerabilities to which the industrial system is exposed, as well as show the technical impact that can be revalued in the original productive context.
Test and demonstration environment in a context of IT/OT convergence to validate the operation of specialised components in industrial cybersecurity
Deploying and maintaining a complex and realistic environment in which to test industrial cybersecurity products, once they have passed the laboratory stage, is very costly, as it requires a great deal of networking and configuration work on several levels and with different technologies. The characteristics of the asset facilitate the creation of scenarios for the analysis of industrial cybersecurity products of all types, both hardware and software, as well as the subsequent demonstration of operation in the integrated environment that an end user may need to make the decision to purchase the component.
Test and demonstration environment in a context of IT/OT convergence to validate the operation of specialised components in industrial cybersecurity
Deploying and maintaining a complex and realistic environment in which to test industrial cybersecurity products, once they have passed the laboratory stage, is very costly, as it requires a great deal of networking and configuration work on several levels and with different technologies. The characteristics of the asset facilitate the creation of scenarios for the analysis of industrial cybersecurity products of all types, both hardware and software, as well as the subsequent demonstration of operation in the integrated environment that an end user may need to make the decision to purchase the component.
ENTITY MANAGING THE ASSET

Contact person:
Raúl Orduna Urrutia
rorduna@vicomtech.org